Once the files were restored a Postmortem meeting was called. We concluded that more restrictions would be placed, banning USB storage devices and personal emails. Also, next year we will be looking into a new Enterprise Antivirus solution and more space will be provided for data backups.
Sunday, 15 November 2015
Week #11: CryptoWall Struck My Job's File Server (Part 3) !
The CrytoWall has been officially removed from our servers! Unfortunately, all backups failed which left the company having to revert to outdated files which is technically, three months old. How we manage to retrieve such data? While that's a long funny story, we had an old decommission server blade that was supposed to be wiped and refurbished three months ago still laying around the server room. Lady luck was on our side because it was the old File Storage server.
Sunday, 8 November 2015
Week #10: CryptoWall Struck My Job's File Server (Part 2) !
Not much as been done with regards to recovering data. We just happen to be extremely lucky that a backup of some of the most vital data was stored on an inactive server. The CrytoWall virus seems to have spread throughout the network. I firmly believe that it was on the network for a very long time, and it was undetected by our antivirus software. This week we have taken some high-risk computers of the network until we find a solution to this vexing problem.
Saturday, 31 October 2015
Week #9: CryptoWall Struck My Job's File Server!
Well, this is a first for me. But, my next two blogs will be based on a real life situation that my job is currently combatting. The dreaded CryptoWall has struck our file storage servers and encrypting all necessary documents and leaving behind a ransom note requiring a cash payment on keys for the decryption.
To address this issue we first need to understand what is a CrytoWall?
CryptoLocker/Wall is a ransomware trojan that targeted computers running Microsoft Windows. CryptoLocker/Wall is transmitted via email attachments, web downloads, and even infected USB drives. The malware could be embedded within your system for long periods until it is triggered. Once, active the malware encrypts a particular type of files stored on local and mounted network drives using an RSA public-key cryptography, with the private key stored on the malware's servers. The malware then displays a message that offers to decrypt the data if a fixed deadline makes a payment. If the deadline is not met, then expect to pay a higher price for the key.
Next week I will give an update how we address this issue...
To address this issue we first need to understand what is a CrytoWall?
CryptoLocker/Wall is a ransomware trojan that targeted computers running Microsoft Windows. CryptoLocker/Wall is transmitted via email attachments, web downloads, and even infected USB drives. The malware could be embedded within your system for long periods until it is triggered. Once, active the malware encrypts a particular type of files stored on local and mounted network drives using an RSA public-key cryptography, with the private key stored on the malware's servers. The malware then displays a message that offers to decrypt the data if a fixed deadline makes a payment. If the deadline is not met, then expect to pay a higher price for the key.
Next week I will give an update how we address this issue...
Sunday, 25 October 2015
Week #8 - Upgrade from Windows XP NOW!
Windows XP should be a thing of the past now, but sadly many users are still having a hard time parting ways of this dead operating system
On April 8th, 2014 Microsoft officially end Windows XP support, but today a strong 250 Million users are still using this operating system.
According to Net Applications, Windows XP users account for nearly 17 percent of worldwide share.
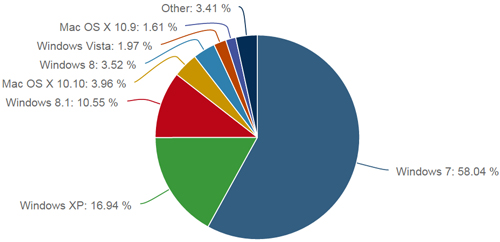
Why should I upgrade?
Windows XP is a security concern. Win XP-based machines are still stable, but Microsoft will no longer roll out security updates for it. That means a computer with OS will be more susceptible to hackers and malware, which could exploit flaws that Microsoft is no longer fixing to gain access to your machine and steal your personal information.
References
Windows XP Usage Still Strong at 250 Million Users ... (n.d.). Retrieved from https://redmondmag.com/articles/2015/04/08/windows-xp-usage.aspx
Why You Should Ditch Windows XP Now | News & Opinion | PCMag.com. (n.d.). Retrieved from http://www.pcmag.com/article2/0,2817,2456104,00.asp
Sunday, 18 October 2015
Week #7 How to make Windows 10 more secure
By default Windows, 10 violates your privacy. When launching Microsoft new browser Edge to search, Bing already knows your location. You notice that all the banner ads are geared toward your hobby.
You’d be surprised by the amount of personal information Windows 10 collects from its users daily. Information such as phone numbers, GPS location, credit card numbers, and even video and audio messages. While, Microsoft’s privacy statement outlines all the data that is collected and how it is used to enhance your experience and claim that the information is safe. Unfortunately, you had to agree to their terms when you downloaded & installed Windows 10 terms of service.
In this Age of the Unread Terms of Service Agreement, it’s important to, read the Terms of Service, Use, and Private Policy. It has become too easy for technologies giants to gather personal information without us realizing it.
Fortunately, Microsoft has incorporated a few settings we could disable to secure our data which is located within the Setting Panel



References
"Hacking Defined Experts | Hacking News & Tutorials."Insert Name of Site in Italics. N.p., n.d. Web. 19 Oct. 2015 <http://www.hackingdefinedexperts.com/.
Windows 10 violates your privacy by default, here's how you ...(n.d.). Retrieved from https://www.yahoo.com/tech/s/windows-10-violates-privacy-default-121036079.html
You’d be surprised by the amount of personal information Windows 10 collects from its users daily. Information such as phone numbers, GPS location, credit card numbers, and even video and audio messages. While, Microsoft’s privacy statement outlines all the data that is collected and how it is used to enhance your experience and claim that the information is safe. Unfortunately, you had to agree to their terms when you downloaded & installed Windows 10 terms of service.
In this Age of the Unread Terms of Service Agreement, it’s important to, read the Terms of Service, Use, and Private Policy. It has become too easy for technologies giants to gather personal information without us realizing it.
Fortunately, Microsoft has incorporated a few settings we could disable to secure our data which is located within the Setting Panel
References
"Hacking Defined Experts | Hacking News & Tutorials."Insert Name of Site in Italics. N.p., n.d. Web. 19 Oct. 2015 <http://www.hackingdefinedexperts.com/.
Windows 10 violates your privacy by default, here's how you ...(n.d.). Retrieved from https://www.yahoo.com/tech/s/windows-10-violates-privacy-default-121036079.html
Sunday, 11 October 2015
Week #6 2013's List of Weak & Common Passwords
If your passwords are displayed here, go change immediately!
Tips on Making Your Password Stronger:
It needs to have 12 Characters, Minimum
Your password should include Numbers, Symbols, Capital Letters, and Lower-Case Letters: Using a mix of different types of characters to make the password harder to crack.
Stay away from obvious dictionary words and combinations of dictionary words.
Don’t use common substitutions, either — for example, “H0use” isn’t strong just because you’ve replaced an o with a 0.
Try to mixing your password up with symbols— for example, Password can be spelled like P@$$W0rD. The use of symbols can be extremely hard to crack.
References
Top 25 most commonly used and worst passwords of 2013 ...(n.d.). Retrieved from http://www.networkworld.com/article/2226175/microsoft-subnet/top-25-most-commonl
Sunday, 4 October 2015
Week #5 Andriod a Liability or an Asset?
Today, Android is the world's most favorite mobile operating system, but it is slowly becoming a liability rather than an asset. The Android platform suffers the issue of fragmentation meaning there are multiple versions of the same operating system on the market, even on newer devices. Manufacturers often make their its own changes to the platform, so they could be behind Google's current reference release. Also, carriers and manufacturers may not update their products' to the updated Android OS version when Google does, or they take months or even years to do so.
As a result, many people within the same organization might be using outdated versions that could be riddled with security vulnerabilities.
Now Android has a new malware that can render the phone useless which is:

References
As a result, many people within the same organization might be using outdated versions that could be riddled with security vulnerabilities.
Now Android has a new malware that can render the phone useless which is:
Android/Lockerpin.A: This is a Malicious apps that disable Android phones until owners pay a hefty ransom. If the user refuses to pay, he/she would have no choice but to do a factory reset, losing all their data.
References
New Android ransomware locks out victims by changing lock ...(n.d.). Retrieved from http://arstechnica.com/security/2015/09/new-android-ransomware-locks-out-victims
Sunday, 27 September 2015
Week #4 Protecting Home Networks
- Computers,
- Gaming devices,
- Smart TVs and;
- Smartphones
To protect your wireless home network you need to have the right tools in place along with educating family members on how to use the Internet safely and securely.
The first step is to Keep a Clean Machine to achieve this an antivirus software is needed to eliminate all threats/ malicious software within the devices. Also, all Internet-enabled devices should have the latest operating system, web browsers, and security software.
Tip for securing Wireless router:
- Change the name of your router
- Change the default password
- Enable router's Firewall
- Limit access to the network by MAC addresses
References
The iGuardian: A Smart Way to Protect Your Home Network.(n.d.). Retrieved from http://www.makeuseof.com/tag/iguardian-smart-way-protect-home-network/
Sunday, 20 September 2015
Week #3 IT Security Planning & Tips for Network Security Planning
The most important part of deployment any type of IT system is planning. Although It is not possible to plan for security with regards to IT, however, a full risk assessment of all system can be performed. Security planning involves developing security policies and implementing controls to prevent computer risks.
Network Security Planning Tips
The biggest threat to a IT security is the people right in that building! Mandatory company training can go a long way towards informing employees of their responsibilities while teaching them best practices for managing IT devices and information.
2. Eliminate the BYOD (Bring Your Own Device) Plan
Don’t allow your employees to deal with company data on personal devices.
3. Restrict Information
Private information should only be available on a need-to-know basis.
4. Maintaining Your Systems
Failing to update computer programs or using outdated computer equipment can create a lot of room for hackers to infiltrate your systems.
5. Have a Disaster Plan
Friday, 11 September 2015
Week #2 What is application security?
Application security is the use of software, hardware, and procedural methods to protect applications from external threats.
 There are many risks associated with developing applications especially if the program will store sensitive data. Below are common Application Security Issues which must be addressed during the development phases of an Application:
There are many risks associated with developing applications especially if the program will store sensitive data. Below are common Application Security Issues which must be addressed during the development phases of an Application:| Input Validation Tampering | A input validation is the outer defensive perimeter for a application. This perimeter protects the logic, processing and output generation. Examples of input validation tampering are cross-site scripting; SQL injection; canonicalization |
Software Tampering | This is when someone modifies the runtime behavior to perform unauthorized actions. |
Saturday, 5 September 2015
How to Keep Your Mobile Devices Secure While Traveling
Because today's smart devices are so much more powerful and can hold so much more information than ever before, the risks of being exploited are increasing. Not to mention that we also have a tendency to carry both personal & business data around with us on the same device, hence making our mobile devices looked so appealing to hackers.
Tips for Keeping Your Mobile Devices Secure
1. Make sure your Mobile Operating software is up-to-date.
2. Use Strong Passwords
3. Avoid unencrypted public Wifi Networks
4. Use VPNs
5. Disable Cookies and autofill
6. Play close attention to 3rd Party Applications security permission changes
Subscribe to:
Comments (Atom)